Why should you study this page: In a SHTF situation... Communications will be critical to your survival...
and The Vigenere Cipher is a simple, practical and effective type of encryption... to be used for secured communications.
The Vigenere Cipher... Print it and learn how to use it.
 Steps to Prepare Msg:
Steps to Prepare Msg:
1. Compose Plaintext Msg.
2. Determine the Key Word or Phrase.
3. Transpose Plaintext letters with Key Word letters... Repeat the Key Word as needed to match Msg Length.
4. For ea Plaintext Msg line... You now have a Key Word Msg Line.
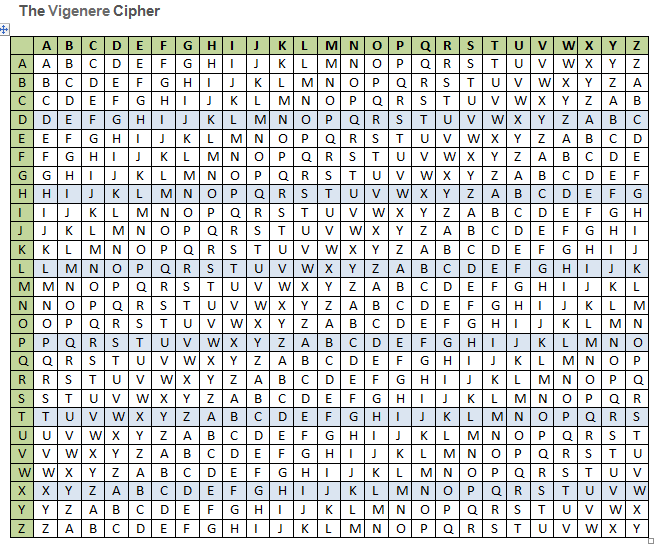
Steps to Encrypt using The Vigenere Table:
1. Encrypt letter by letter to form the Ciphertext Line
2. Use/find Plaintext letters across the Top Row.
3. Use/find Key Word letters down the Left Side Column.
4. Follow the vertical column for the Plaintext letter and the horizonal row for the Key letter to
determine the intersecting cell/letter.
5. Apply the intersecting letter to the ciphertext line.
Steps to Decrypt using The Vigenere Table:
1. Still Decrypt letter by letter to form the Plaintext Line
2. Still Use/find Key Word letters down the Left Side Column.
3. On the Key Letter Row... Locate the Ciphertext letter
4. Then follow the vertical column up to the Top Row to determine the Plaintext letter.
5. Apply the Top Row letter to the Plaintext line.
 Steps to Cipher using Math:
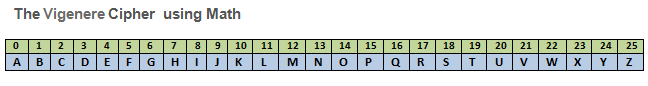
Steps to Cipher using Math:
1. Prepare the Msg as shown above
2. Use/find Plaintext or Ciphertext letter and find the corresponding numeric value.
3. Use/find Key Word letter and find the corresponding numeric value.
4. To Encrypt... Add the math value for the 2 cipher letters... If < 26... Simply find the corresponding letter value.
If > 26... then subtract 26... before finding the corresponding letter value.
5. To Decrypt... Subtract the math value for the 2 cipher letters... If > 0... Simply find the corresponding letter value.
If < 0 (negative)... then add 26... before finding the corresponding letter value.
For some, Using the Math Modulus 26 table will be faster and simpler once they fully understand the concept.
Study and learn the preceding intructions for a SHTF case... A computer assisted mode is provided below:
Note: No Key Words or Data entered here are saved or stored in our Database... You can use copy/paste to post
a private Q & A or paste it in an encoded email.
Encrypt or Decrypt:
Key Word or Phrase:
Message Text... (Plain text or Encoded):
Cipher
Reset
This is your encoded or decoded text:
